OpSyria: Hand-crafted phishing to chase Syrian activists
How the lamest ever phishing tool can kill Syrians. Reflets has been continuously warning that several major western manufacturers were selling - directly or not - monitoring equipment to dictatorial regimes.

Reflets has been continuously warning that several major western manufacturers were selling - directly or not - monitoring equipment to dictatorial regimes. This includes the French company Amesys that provided Libya with their famous mass-monitoring system Eagle, the Italian brand Area SpA that may be about to install the same kind of devices for the Syrian regime (using technology produced by the French company Qosmos), and of course the American company Blue Coat, having at least twenty of their ProxySG devices in Syria to monitor and censor the Web. All these tools have been used for years to arrest opponents who were expressing their opinions too freely on the Internet.
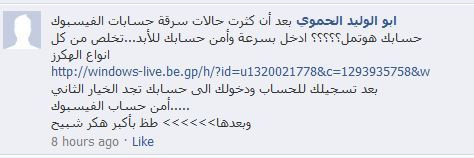
Far from those high-tech devices involving thousand-euro contracts, Assad's thugs, the now famous Mukhabarat and Shabeeha, also benefit from amateurish Web developers to steal opponents' logins and passwords on main social media and e-mail providers. And this might be even more efficient than expansive monitoring equipments.
Details on a website that is practising the "business of phishing" follow. The bell was rang by several Syrian Telecomix agents, who had noticed that the link was spread on several Syrian Revolution Facebook pages by untrusted people.
Account Hacking Made Easy
A developer promotes his phishing service in a video posted on YouTube, showing how easy it is to create...