#OpSyria : Why #BlueCoat lied ?
For a few days, Reflets has been looking forward an official denial of the presence of filtering appliances in Syria. Their website did not mention the torrential articles published after our revelations. Neither in the "Press Release", for a denial, nor, - of course - in the "Blue Coat in the News", while BlueCoat was the object of many articles about the presence of its appliances in Syria... Fair enough. But we could have at least expected a disclaimer, a tricky catchphrase.

A few weeks ago, Telecomix, Reflets and FHIMT started OpSyria, an operation aimed to establish direct contacts with Syrian population. We hoped to empower them with means to anonymize their communications, and therefore, to inform us about the situation in the country. Through "Forcing" Internet users of this country to connect to an explanatory page, we have been able to talk with them on an IRC channel (the ancestor of instant messaging). "Forcing" Internet users of this country to connect to our information page, first had implied sort of Syrian Internet's topography. It is during this mapping that Telecomix found appliances (big boxes that make "stuff" to IP packets that travels over the network) from the BlueCoat company. Looking at traces, accessible without hacking machines, it appears that these servers are used by Syria to filter the content displayed to Syrian Internet users. Asked by an Internet user, Steve Schick, a member of BlueCoat's telecommunication department issued the following disclaimer::
"Blue Coat does not sell to Syria and neither do we provide any kind of technical support, professional services or software maintenance. To our knowledge, we do not have any customers in Syria. _U.S. companies are prohibited from selling to Syria. In addition, we do not allow any of our resellers, regardless of their location in the world, to sell to an embargoed country, such as Syria.__ We have seen logs posted that are allegedly from a Blue Coat appliance in use in Syria. From these logs, we see no firm evidence that would determine there is Blue Coat equipment in Syria; in fact, it appears that these logs came from an appliance in a country where there are no trade restrictions. In addition, the log files appear to have come from a third party server that was storing log files uploaded from one of our appliances. The allegation that an organization penetrated one of our appliances through a security hole is flatly not true. There are no known vulnerabilities of our appliance that would allow such an action."_
It is important to dissect this statement accurately, word by word.
"Blue _ Coat does not sell to Syria and neither do we provide any kind of technical support, professional services or software maintenance. To our knowledge, we do not have any customers in Syria._"
This part is quite plausible, as we stated it in our first article. BlueCoat's appliances could have transited by an other country, from an absolutely legitimate buyer, thought this is BlueCoat's point of view. Then, someone would have acted as an intermediate in order to avoid USA's embargo on Syria.
What's more, an HTTP access observed through tcpdump :
17:40:47.946109 IP 82.137.200.48.55929 > 88.191.132.173.80: P 0:221(221) ack 1 win 1032 <nop,nop,timestamp 1854495731 1793229197> _E...,7..,.i.R..0X....y.P.s..8.!.....4......__ n.[.j...HEAD /guidelines_EN-AR.odt HTTP/1.1 User-Agent: Microsoft Office Existence Discovery Host: telecomix.ceops.eu Content-Length: 0 X-Forwarded-For: 31.9.54.40 Connection: Keep-Alive X-BlueCoat-Via: AACDEBEFA2CBA614_ -- Explanations : 82.137.200.48 : BlueCoat IP Adress 88.191.132.173 : http's server IP from where the request is send X-Forwarded-For: 31.9.54.40 <- user's IP that make the request X-BlueCoat-Via: AACDEBEFA2CBA614 <- BlueCoat's device unique ID that transmitted the request
Hey Mr. blueCoat ... Is it the word Syria or BlueCoat that you don't understand in this log?
"U.S. companies are prohibited from selling to Syria. In addition, we do not allow any of our resellers, regardless of their location in the world, to sell to an embargoed country, such as Syria."
That's an interesting statement , if it was proved wrong, BlueCoat would be in a disagreeable situation in the United states after having uttered it.
For example, BlueCoat could refer to some Linkedin profiles who don't quite think the same way. E.g : the man tells about some projects which were conducted in Syria
Senior Network Engineer Advanced Technologies System www.ats (Sole Proprietorship) _ Sole Proprietorship; Telecommunications industry __ January 2010 – February 2011 (1 year 2 months) ATS is recognized as a dynamic and innovative information technology company.The company is active throughout Syria; with a strong network of partners and VARs.The company's primary drivers are client care, client satisfaction, the honoring of all commitments, the development of our employees and an absolute commitment to integrity Job Responsibilities Responsible for designing and implementation of customers networks_ Implement Cisco Security solutions | Bluecoat Appliances Installation and maintenance Barracuda Appliances installation and maintenance _Mitel IP Telephony solutions installations and maintenance__ Build and maintain Visio network documentations for Clients_ Help establish guidelines and standards for Change Procedures Routing Protocol RIP, EIGRP, OSPF, BGP. Supporting Procurement team to purchase Hardware and Software from multiple vendors _Project Design and Implemented:__ Albaath University Network Design and Installation and maintenance (Network from about 5000 Node) which include cisco and bluecoat and Barracuda Technologies**Tarassul ISP (ISP with about 30000 Broadband Customer) Caching System Design and installation** _PORTO Village Tartous IPT installation and integration with opera ( about 500 Ext)Many IPT installations for small Companies (less than 200 EXT) Senior Project Engineer iNet ISP Privately Held; 51-200 employees; Internet industry _September 2009 – December 2009__ (4 months) Network Engineering Team INET is one of big ISP's in Syria since 2006 which is spicialest in Providing internet for corporate Section. Job Responsibilities Responsible for designing and implementation of customers network infrastructure_ Help negotiate hardware, software, and circuit contracts for customers Build and maintain Visio network documentations for Clients Implementation of TCP/IP & related Services-DHCP/DNS/WINS Build and maintain Visio documentation database of network topology Help establish guidelines and standards for Change Procedures Supporting Procurement team to purchase Hardware and Software from multiple vendors _Professional Training For company customers__ Project executed: Damascus University Security Project : which include installation for Barracuda web filter in all University Parts and Spam Firewall in University datacenter and Bluecoat Packet Shaper on university internet gateway _ Cisco IPS Training for Damascus University Team _CISCO NAM2 Training for university Team Senior Project Engineer_ Syrian Data Systems Information Technology and Services industryAugust 2008 – August 2009 (1 year 1 month)SDS is IT solutions provider in Syria since 1994, and part of INANA Group Job Responsibilities _Responsible for designing and implementation of customers network infrastructure_ Responsible for VOIP Solutions Help negotiate hardware, software, and circuit contracts for customers Build and maintain Visio network documentations for Clients Implementation of TCP/IP & related Services-DHCP/DNS/WINS Help establish guidelines and standards for Change Procedures Supporting Procurement team to purchase Hardware and Software from multiple vendors_ Professional Training For company customers Managing customer expectation through proactive updates during project lifecycle. Handover services to assurance team on completion of the project has been offered to our customers and deliver the solution. Project executed: Damascus university Core Network : this project include 6500 Core Switch with FWSM and IDSM-2 and NAM module and 7600 Router and many other Cisco series and wan Technology and bluecoat Proxy etc. .. Peering between tow bigger ISP\s in Syria Tarassul and 190 using BGP Damascus Security Exchange IPT with integration with Recording and billing solution_Many other data Network and IPT Installations and maintenance
Tell me, Mr BlueCoat, obviously its not zero, neither one, but many clients that you have in Syria. Any issues with your client database ?
But, let's get back to BlueCoat's denial :
We have seen logs posted that are allegedly from a Blue Coat appliance in use in Syria. From these logs, we see no firm evidence that would determine there is Blue Coat equipment in Syria; in fact, it appears that these logs came from an appliance in a country where there are no trade restrictions. In addition, the log files appear to have come from a third party server that was storing log files uploaded from one of our appliances.
Those logs came from a machine which is on the IP range : 82.137.200.XXX. Then, unless the Whois databases were corrupted by some army of chinese cyberterrorist, the Whois range give us this :
Netname: SY-ISP-TARASSUL _descr: Tarassul inetnet Service Provider__ country: SY admin-c: FA1765-RIPE tech-c: AS4007-RIPE status: ASSIGNED PA mnt-by: STEMNT-1 source: RIPE # Filtered person: Firas Ahmad address: Syrian Telecommunication Est address: Damascus, Syria phone: +963-11-3739748 fax-no: +963-11-3739765 e-mail: feras.ahm@tarassul.sy nic-hdl: FA1765-RIPE mnt-by: STEMNT-1 source: RIPE # Filtered person: Ali Saleh address: Syrian Telecommunication Est address: Damascus, Syria phone: +963-11-3739748 fax-no: +963-11-3739814 e-mail: ali.s@tarassul.sy nic-hdl: AS4007-RIPE mnt-by: STEMNT-1_source: RIPE # Filtered
"In addition, the log files appear to have come from a third party server that was storing log files uploaded from one of our appliances."
There are two interesting points here. The first on concerns information that BlueCoat had in hand to declare such a thing. How could BlueCoat, who has absolutely no direct link with Syria, neither through a reseller, know that logs came from one of their appliances (that is supposedly located outside Syria) but has been uploaded on other machine ?
In addition, these logs are actually driven on FTPs from an appliance. Except that the FTP is very close the appliance. The appliance is on an address range from Tarassul. FTP too:
"The allegation that an organization penetrated one of our appliances through a security hole is flatly not true. There are no known vulnerabilities of our appliance that would allow such an action."
So there .... It peaked. Before starting, we must understand that the logs from BlueCoat's Syrian appliances were not downloaded through hacking techniques. It was available unprotected. For free download, the only product of incompetence of the administrator that configured the machine. If we were talking about in this precise case, it would be exclusively a human failure. Now, regarding security issues, technical those ones, that doesn't exist at BlueCoat's : :
- http://www.exploit-db.com/exploits/17883/
- http://www.exploit-db.com/exploits/17513/
- http://www.exploit-db.com/exploits/17883/
... to fetch only these one.
RESSOURCES
- BlueCoats's IPs (suspected, at least)
82.137.200.42 82.137.200.43 82.137.200.44 82.137.200.45 82.137.200.46 82.137.200.47 82.137.200.48 82.137.200.49 82.137.200.50 82.137.200.51 82.137.200.52 82.137.200.53 82.137.200.54 82.137.200.55 82.137.200.56 77.44.210.15 90.153.128.14 90.153.128.15
==================
The Statement :
- http://yro.slashdot.org/story/11/10/11/1629238/US-Security-Company-Blue-Coats-Devices-Helping-Syrian-Govt
- http://www.zdnet.co.uk/blogs/security-bullet-in-10000166/blue-coat-web-filtering-technology-used-by-syria-10024276/
- Summary : http://advocacy.globalvoicesonline.org/2011/10/10/bluecoat-us-technology-surveilling-syrian-citizens-online/
==================
==================
- Syrian PRTG with some BlueCoat devices :http://213.178.224.130/prtg.htm
==================
- http://b.averysmallbird.com/entries/bluecoat-and-syria-indicators-and-culpability : interesting as it appears that in the logs, there is evidence that the appliance calls home (BlueCoat) for URL rating
==================
- Nmap outputs :
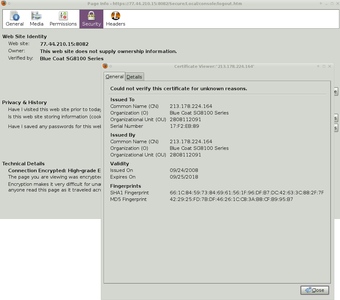
This is a nmap scan result executed from Europe towards 77.44.210.15, which is a Syrian IP belonging to the Syrian Computer Society. See http://whatismyipaddress.com/ip/77.44.210.15 for more details. ---
# nmap -A -O 77.44.210.15Starting Nmap 5.51 ( http://nmap.org ) at 2011-10-12 13:38 CESTNmap scan report for 77.44.210.15Host is up (0.13s latency).Not shown: 985 closed ports _PORT STATE SERVICE VERSION__ 22/tcp filtered ssh 23/tcp filtered telnet 53/tcp open domain? 80/tcp open http Blue Coat proxy server |_http-title: Access Denied|_http-methods: No Allow or Public header in OPTIONS response (status code 403)81/tcp open http-proxy BlueCoat SG-400 http proxy 135/tcp filtered msrpc 139/tcp filtered netbios-ssn 1720/tcp filtered H.323/Q.931 1723/tcp filtered pptp 2000/tcp filtered cisco-sccp 3128/tcp open http Blue Coat proxy server|_http-methods: No Allow or Public header in OPTIONS response (status code 403)|_http-title: Access Denied 4444/tcp filtered krb524 5060/tcp filtered sip 8080/tcp open http Blue Coat proxy server |_http-title: Access Denied|_http-methods: No Allow or Public header in OPTIONS response (status code 403)8082/tcp open ssl/http Blue Coat SG210 http proxy config |_sslv2: server still supports SSLv2 |_http-title: Site doesn't have a title (text/plain; charset=utf-8). | http-auth: HTTP/1.1 401 Authentication Required |_ |_Basic realm=77.44.210.15 _1 service unrecognized despite returning data. If you know the service/version, please submit the following_ fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :_ SF-Port53-TCP:V=5.51%I=7%D=10/12%Time=4E957C47%P=i686-pc-linux-gnu%r(DNSVe SF:rsionBindReq,44,"B\x06\x85\x01\x01\x01\x07version\x04bi SF:nd\x10\x03\xc0\x0c\x10\x03\n\t[secured]\xc0\x0cSF:\x02\x03\x02\xc0\x0c");Device type: WAP|general purpose|phone|proxy serverRunning (JUST GUESSING): Netgear embedded (92%), FreeBSD 6.X|7.X|5.X (90%), Apple iPhone OS 3.X (87%), Apple Mac OS X_ _10.5.X|10.6.X|10.4.X|10.3.X (87%), Blue Coat SGOS 5.X (86%)Aggressive OS guesses: Netgear WGR614v7 wireless broadband router (92%), FreeBSD 6.2-RELEASE (90%), FreeBSD_ 7.0-CURRENT (90%), FreeBSD 5.4-RELEASE (89%), FreeBSD 6.3-RELEASE (89%), FreeBSD 6.0-STABLE - 6.2-RELEASE (88%), Apple iPhone mobile phone (iPhone OS 3.0 - 3.2.1, Darwin 10.0.0d3) (87%), Apple Mac OS X 10.5.2 - 10.6.2 (Leopard - Snow Leopard) (Darwin 9.2.0 - 10.2.0) (87%), Apple Mac OS X 10.6.2 (Snow Leopard) (Darwin 10.2.0) (87%), Blue Coat SG510 proxy server (SGOS 5.2.2.5) (86%)No exact OS matches for host (test conditions non-ideal).Network Distance: 15 hops _Service Info: OS: SGOS; Device: proxy server__ TRACEROUTE (using port 256/tcp) HOP RTT ADDRESS 1 20.23 ms 10.7.2.1 2 30.41 ms 10.8.48.1 *** HOPS 3-8 STRIPPED FOR PRIVACY *** 9 134.65 ms 80.156.162.194 10 120.87 ms 82.137.192.205 11 ... 12 143.63 ms 10.1.100.2 13 152.90 ms 172.19.1.2 14 152.87 ms 77.44.201.206 15 135.43 ms 77.44.210.15 OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ ._Nmap done: 1 IP address (1 host up) scanned in 54.48 seconds
Nmap scan done from Europe. Towards 90.153.128.14 which is Syrian IP.** Shows BlueCoat SG810 proxy.**
--- _# nmap -A -O 90.153.128.14__ Starting Nmap 5.51 ( http://nmap.org ) at 2011-10-12 14:27 CEST Nmap scan report for 90.153.128.14 Host is up (0.13s latency). Not shown: 832 closed ports, 166 filtered ports PORT STATE SERVICE VERSION 3128/tcp open tcpwrapped 8000/tcp open tcpwrapped Device type: proxy server Running (JUST GUESSING): Blue Coat SGOS 4.X (86%)Aggressive OS guesses: Blue Coat SG810 proxy server (SGOS 4.2.3.26) (86%)No exact OS matches for host (test conditions non-ideal). Network Distance: 21 hops TRACEROUTE (using port 5900/tcp) HOP RTT ADDRESS 1 10.05 ms 10.7.2.1 2 60.92 ms 10.8.48.1 *** 3-9 STRIPPED ***10 119.68 ms if-7-2.tcore1.FNM-Frankfurt.as6453.net (195.219.50.2)11 142.98 ms if-5-2.tcore1.AV2-Amsterdam.as6453.net (195.219.194.13)12 142.93 ms if-2-2.tcore2.AV2-Amsterdam.as6453.net (195.219.194.6)13 142.89 ms if-5-2.tcore2.L78-London.as6453.net (80.231.131.13)14 64.06 ms if-4-0-0.mcore3.L78-London.as6453.net (80.231.131.34)15 123.59 ms if-0-3-0.core1.CYR-Cairo.as6453.net (195.219.48.174)16 142.99 ms ix-3-1-1.core1.CYR-Cairo.as6453.net (41.206.189.22)17 143.05 ms 82.137.192.209 18 ... 19 143.12 ms 10.1.100.22 20 143.12 ms 172.16.1.10 21 132.46 ms 90.153.128.14 OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 31.03 seconds_
# nmap -A -O 90.153.128.15
Starting Nmap 5.51 ( http://nmap.org ) at 2011-10-12 14:42 CEST _Nmap scan report for 90.153.128.15__ Host is up (0.14s latency). Not shown: 833 closed ports, 166 filtered ports PORT STATE SERVICE VERSION 1755/tcp open wms? Device type: proxy serverRunning (JUST GUESSING): Blue Coat SGOS 4.X (85%)Aggressive OS guesses: Blue Coat SG810 proxy server (SGOS 4.2.3.26) (85%)No exact OS matches for host (test conditions non-ideal).Network Distance: 21 hopsTRACEROUTE (using port 3306/tcp)HOP RTT ADDRESS 1 30.16 ms 10.7.2.1 2 66.32 ms 10.8.48.1 *** 3-9 SKIPPED *** 10 121.42 ms if-7-2.tcore1.FNM-Frankfurt.as6453.net (195.219.50.2)11 142.57 ms if-5-2.tcore1.AV2-Amsterdam.as6453.net (195.219.194.13)12 142.42 ms if-2-2.tcore2.AV2-Amsterdam.as6453.net (195.219.194.6)13 122.34 ms if-5-2.tcore2.L78-London.as6453.net (80.231.131.13)14 142.46 ms if-14-0-0.mcore3.L78-London.as6453.net (80.231.131.10)15 142.41 ms if-0-3-0.core1.CYR-Cairo.as6453.net (195.219.48.174)16 142.51 ms ix-3-1-1.core1.CYR-Cairo.as6453.net (41.206.189.22) 17 142.54 ms 82.137.192.209 18 ... 19 142.60 ms 10.1.100.10 20 142.61 ms 172.16.1.10_21 134.10 ms 90.153.128.15
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 83.98 seconds

